
UpGrade IT doesn’t just offer cookie-cutter solutions. We understand that every building has unique security needs. That’s why we provide custom-designed access control systems tailored to your specific requirements. Our process begins with detailed CAD drawings that map out your building and pinpoint ideal locations for access points, readers, and controllers. Our expert team works closely with you from the initial design phase through to the final installation, ensuring a seamless integration with your existing infrastructure. This personalized approach guarantees a robust, efficient, and user-friendly access control system that perfectly matches your building’s layout and security objectives.
Mandatory Access Control (MAC) is a highly secure cybersecurity model that goes beyond simple usernames and passwords. It uses labels and clearances to classify both users and data, ensuring that only authorized individuals can access sensitive information. Think of it as a strict hierarchy where data is compartmentalized based on its sensitivity. By partnering with UpGrade IT, your business gains expert implementation and management of MAC, bolstering your data protection against unauthorized access and internal threats. Our tailored solutions ensure seamless integration with your existing systems while adhering to industry best practices and regulatory compliance requirements. With UpGrade IT, you get robust, proactive security that protects your valuable assets and enhances your business's overall security posture
Discretionary Access Control (DAC) puts access control decisions in the hands of data owners. 1 This flexible model allows individuals with access rights to grant or revoke permissions to others based on their discretion
Role-Based Access Control (RBAC) simplifies user management by assigning permissions based on roles within your organization. Instead of granting access to individuals one by one, you assign permissions to specific roles like “manager,” “accountant,” or “sales representative.” Employees are then assigned to these roles, inheriting the corresponding permissions.
Partnering with Upgrade IT for your security floor plan design brings expert knowledge and cutting-edge technology to protect your assets. Our team considers your building’s unique layout, entry/exit points, and potential vulnerabilities to create a customized plan. We integrate advanced access control systems, strategically placed surveillance, and robust alarm systems, ensuring comprehensive security coverage. Upgrade IT also prioritizes compliance with safety regulations and building codes, guaranteeing a secure and legally sound environment. By collaborating with Upgrade IT, you gain a reliable partner dedicated to safeguarding your premises and ensuring peace of mind.
Beyond immediate security, a strong floor plan improves operational efficiency. Clear pathways, designated zones, and optimized layouts streamline movement and workflow. This leads to increased productivity, reduced response times during emergencies, and a more organized and functional space overall. By prioritizing a security floor plan, you proactively invest in both safety and operational excellence.
Investing in a well-designed security floor plan offers significant benefits. Primarily, it enhances protection for your valuable assets, employees, and visitors by deterring criminal activity and minimizing risks. A comprehensive plan with strategically placed security measures like surveillance, access control, and alarm systems creates a safer environment and reduces the likelihood of theft, vandalism, and unauthorized access.

AI-powered security cameras represent a significant leap forward in surveillance technology, offering a range of benefits over traditional systems. Here’s a breakdown of why they’re becoming increasingly important:
Enhanced Accuracy and Efficiency:
Advanced Analytics and Automation:
Increased Safety and Security:
AI Camera Applications:
Advanced Access Platform
A centralized building access management system provides a single, unified platform to control access across your entire facility. This eliminates the need for disparate systems and manual processes, simplifying security management and reducing administrative overhead. Security personnel can easily monitor access points, grant or revoke credentials, and respond to incidents from a central location.
By automating access control processes, a centralized system saves time and resources. Employees can use a single credential for access to various areas, eliminating the need for multiple keys or cards. This streamlines movement throughout the building, improving efficiency and productivity.
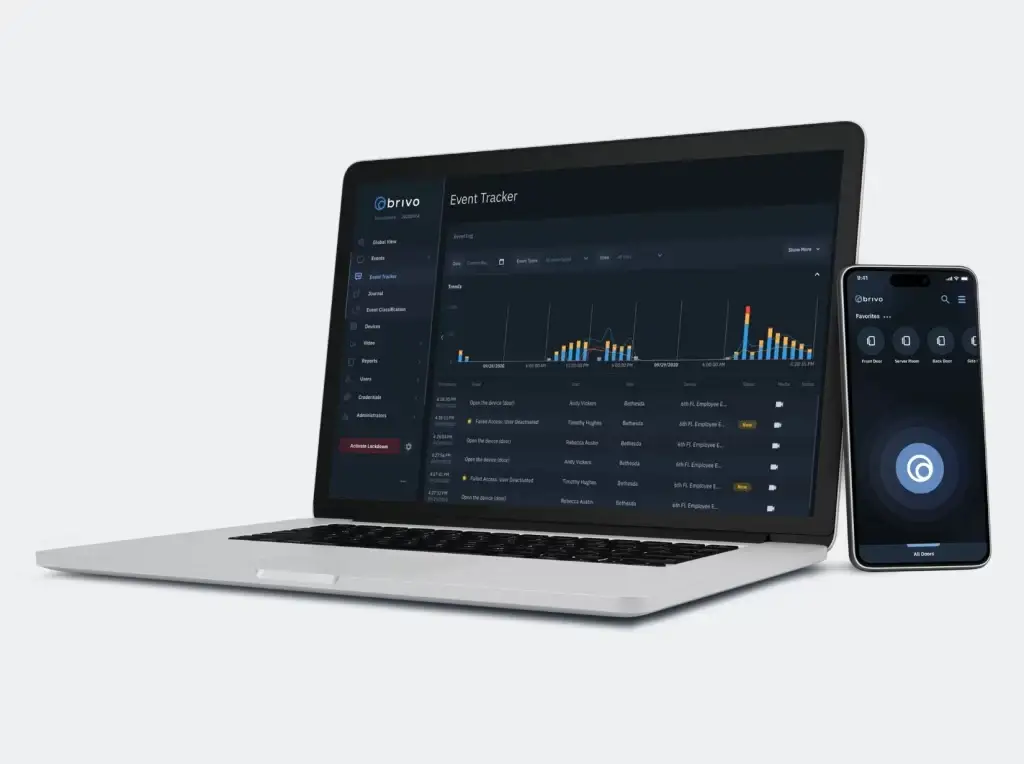
Centralized systems offer granular control over who accesses what and when. You can easily assign different levels of access permissions to employees, visitors, and contractors based on their roles and needs. This strengthens security by preventing unauthorized entry to sensitive areas and protecting valuable assets.
Centralized systems provide real-time visibility into access events across your building. You can track entries and exits, monitor access attempts, and generate detailed reports for analysis and audit trails. This real-time data enhances situational awareness and enables proactive security management.
10050 112 St NW
Edmonton, Alberta
587-398-0013
info@upgradeit.ca
Mon- Fri: 9am- 6pm
Saturday: 10am-4pm

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.