Upgrade IT elevates your business security with AI-powered access management solutions, seamlessly integrated with Building Management Systems (BMS) and fire alarm networks. Experience enhanced security, reduced human error, and improved efficiency. Our cutting-edge solutions offer real-time monitoring and predictive maintenance, ensuring your facility is always protected.

Identification is the crucial first step in access control, where individuals are verified and assigned a unique identity within a system. This process can be challenging, especially in large-scale environments. Two primary methods are used for identification: user IDs and badges. User IDs are unique identifiers assigned to individuals, allowing for activity tracking and personalized access. These IDs should be secure and not reveal any personal information. Badges, on the other hand, provide physical identification through cards or tags containing visual information like photos and names, enabling quick verification and access control in physical spaces.

Access control systems secure information by verifying and authorizing user access based on their identity and role. Authentication, a key component, confirms users are who they claim through methods like passwords or biometrics. Strong passwords and multi-factor authentication enhance security, while biometrics offer a convenient and robust alternative with higher security but require specialized equipment.

Authorization determines who has access to what resources. It follows identification and authentication, defining user permissions within a system. Two primary methods exist: access control lists (ACLs) and role-based access control (RBAC). ACLs specify exact resources a user can access, offering flexibility but potentially becoming complex to manage. RBAC simplifies administration by assigning permissions based on user roles, though careful planning is needed to define roles and their associated permissions.
These are the tools used to identify individuals, such as key cards, fobs, mobile credentials, or biometrics (fingerprint, facial recognition).
Devices installed at entry points to read the credentials and transmit the information to the control panel.
The brain of the system, receiving information from readers, processing it, and triggering actions (granting or denying access).
Includes electronic locks, strikes, and magnetic locks that physically control the opening and closing of doors.
Push buttons, motion sensors, or crash bars that allow for safe and easy egress from the building. .
The interface that allows administrators to manage the system, add or remove users, assign permissions, and monitor activity.
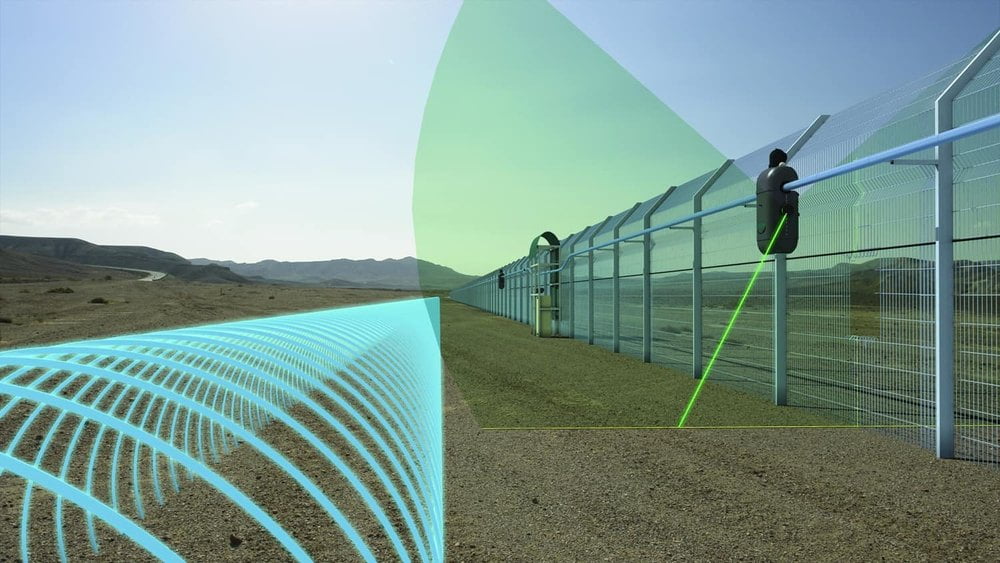
Secure your perimeter with our advanced fence sensors, engineered for unparalleled reliability. Unlike standard systems, our sensors intelligently differentiate between genuine threats and harmless environmental factors. They accurately detect cut or climb attempts, triggering immediate alerts, while effectively filtering out disturbances from wind, rain, or passing vehicles.
This sophisticated technology maximizes detection probability, ensuring your property remains protected, and minimizes nuisance alarms, providing you with peace of mind and efficient security management.
Biometric access control takes building security to the next level. By using unique biological traits like fingerprints or facial recognition, it ensures that only authorized individuals gain entry. This eliminates the risks associated with traditional keys or cards, which can be lost, stolen, or shared. Biometrics provides superior accuracy, accountability, and convenience, giving you complete peace of mind about who has access to your premises.
Partner with Upgrade IT to safeguard your most valuable assets – your people and property. We go beyond basic security solutions, designing and implementing comprehensive systems tailored to your unique needs. Our expertise in integrated security technologies, including access control, video surveillance, and intrusion detection, ensures a robust defense against potential threats. With Upgrade IT, you gain a trusted partner dedicated to protecting your business and providing you with peace of mind.
10050 112 St NW
Edmonton, Alberta
587-398-0013
info@upgradeit.ca
Mon- Fri: 9am- 6pm
Saturday: 10am-4pm

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.